All that changed with the growth of the personal computer. It became cheaper and easier to provide each desk-jockey and even executives with a basic IBM-style desktop computer. However, this necessarily came with connections to the external world - first a cassette-recorder interface (dropped in the 1980s) and 5.25" exchangeable disk drives, followed by 3" and 3.5" disk drives and then the USB interface. Each development enabled successively smaller exchangeable media. Coupled with opening up the World Wide Web as well as organisations' internal network, a headache for data controllers was created.
It has been a short step to providing not just an organisation-owned physical machine on the desktop but also wireless access to corporate facilities via a user's own device - lap-top computer, tablet or smartphone. When the lines between private and corporate facilities become blurred, we reach the situation in which Mrs Clinton has found herself. I believe she is merely the most high-profile example of careless crossing of boundaries which occurs day-by-day in companies, councils and government.
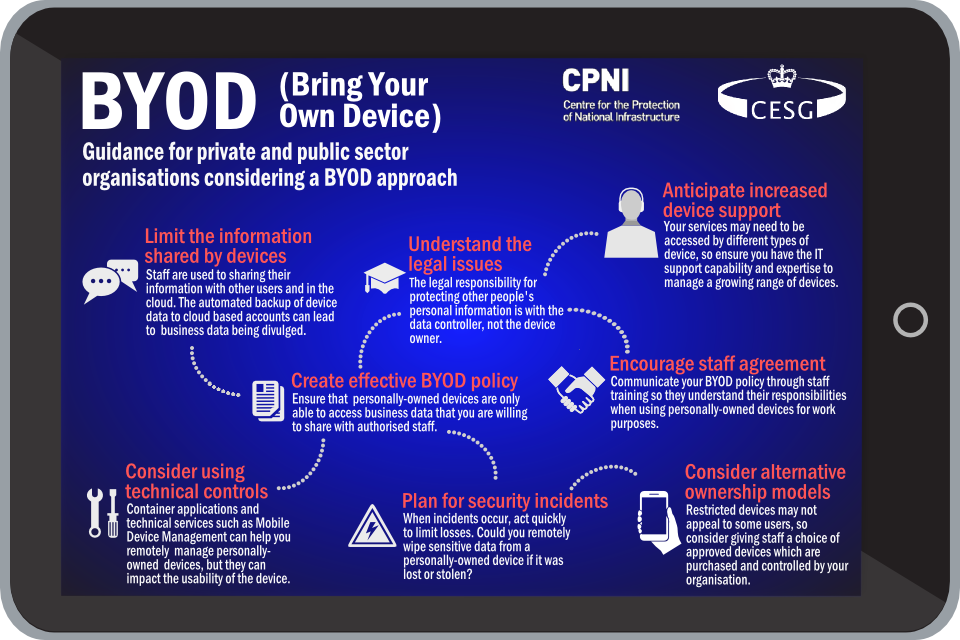
It is clearly essential that organisations holding or with access to third-party data, as well as their own sensitive information, have strict policies on BYOD (or "bring your own technology" as it sometimes described) and it is good to see that government has issued guidelines.
No comments:
Post a Comment